The recent tragic events in Uvalde, Texas have prompted renewed discussions about school safety. Ideas and solutions are batted around by politicians, news anchors, and your next-door neighbor. I heard one radio host claim that what makes these events so tragic is that we cannot prevent them.
That’s simply untrue. As reported in the wake of the shooting, there were numerous “red flags” surrounding the shooter—he had recently been placed with his grandmother, he was bullied, other students called him “school shooter,” etc. The process of behavioral threat assessments allows a trained school team to look at red flags like these, assess the risk, and get that student off a pathway to violence.
One common behavioral threat assessment model defines threat assessment as a problem-solving approach to violence prevention. This approach involves assessment and intervention with students who have threatened violence in some way[1]. While some states require schools to have a behavioral threat assessment team and process in place, many do not. Fortunately, there are various models available to schools that are interested, such as the Salem-Keizer model, the Comprehensive School Threat Assessment Guidelines (CSTAG) model, the Kris Mohandie model, and more.
Regardless of the model, behavioral threat assessment gives educators a process for assessing the “red flags” that are reported to them. But how exactly does that assessment process work? A school threat assessment team is trained to determine whether a threat is serious or not. Staff learn how to conduct interviews and communicate with individuals who have witnessed a specific threat or threatening behaviors. Oftentimes, information exists in silos—a teacher may feel nervous about an essay she received from a student; a classmate overhears an angry outburst from a fellow student; or a student makes “creepy” comments that leave others feeling uncomfortable. If a school has a process in place that allows these parties to submit their concerns, then a team can review the collected information and intervene as necessary.
That concept—intervention—is a critical part of behavioral threat assessment. If a threat exists, how do you keep the student off the pathway to violence? The team can look at the risk factors in the student’s life and figure out what tools and resources he or she might need. The student might benefit from counseling, daily check-ins with staff, a change in buses or classes, etc. (While threat assessment may help inform the disciplinary process, it is not considered to be part of discipline.)
For threat assessment to be effective, it has to be properly implemented. Districts may dedicate time to sending staff to all-day trainings, but if there’s no plan for how to implement lessons learned when they return, little progress will be made. In particular, staff, students, and community members need to know the process for reporting and responding to threats. This will help build confidence that threats are taken seriously, and that the district is being proactive rather than reactive.
Let’s conclude by reiterating some seldom-acknowledged good news: School violence can be prevented. Furthermore, the benefits of a behavioral threat assessment approach to prevention far outweigh what little costs there might be for training and implementation. The following, posted on the CSTAG website, is reason enough for schools to take this approach seriously:
Our research, conducted through the University of Virginia and published in peer-reviewed scientific journals, shows that schools using threat assessment have resolved thousands of threats without serious injury. Moreover, schools using our model of threat assessment have substantial reductions in the use of school suspension and lower rates of bullying. On school climate surveys, students and teachers report feeling safer than in schools not using threat assessment. Finally, school staff representing administration, instruction, mental health, and law enforcement all report high levels of satisfaction, knowledge, and motivation regarding the use of threat assessment...[2]
[1] Adapted from: https://www.schoolta.com/
[2] Adapted from: https://www.schoolta.com/
*The views and opinions expressed in the Public Risk Management Association (PRIMA) blogs are those of each respective author. The views and opinions do not necessarily reflect the official policy or position of PRIMA.*

By: Kaylee Sorensen
Emergency Management Consultant, Ashton Tiffany
Kaylee Sorensen has worked for Ashton Tiffany and its acquiring company, RPA, for 10 years. In 2017, she launched an emergency management program for Ashton Tiffany’s largest client, the Arizona School Risk Retention Trust (the Trust). For Trust members, Kaylee has facilitated regional safety consortiums around the state, assisted with the development of emergency operations plans, assessed drills and exercises, and more. Kaylee has also partnered with various public agencies across Arizona to promote interagency cooperation in emergency management.
Some time ago, while attending a division’s recent accident review board for a vehicle accident involving significant loss from a single vehicle accident, I was struck by the fact that even though the loss was significant with serious potential for injury, neither the division head or the assistant were in attendance. The committee was chaired by a first line supervisor who seemed to struggle with the consequences before him, a large loss that initially appeared preventable barring any contributions from failed road maintenance. The process in this example was lacking while there was so much opportunity for management to participate, to positively impact employees by attending and participating in the accident investigation process.
First, the attendance of senior leadership demonstrates to employees that the leadership has a vested interest in their personal safety. If conveyed effectively, not utilizing the investigation merely as fault finding, the presence of senior leadership demonstrates that managers do care about employees and that managers do want to utilize the investigation as a mutual commitment to prevent injuries. Of course, it is most meaningful when managers follow up and act and make changes as needed.
Secondly, participation in accident reviews provides senior staff first hand information not only on the accident’s initial causes but also circumstances that may have contributed to the unfortunate event. Could it be that policy contributed to an injury? Or inadequate equipment or an ineffective process? Is wearing a plastic hard hat at all times in a Virginia summer outdoors reasonable if there are no inherent hazards? What is the employees “black box” process, what they really do instead of following the policy? There are other forms of communication for senior staff to engage employees but where a critical incident occurs, the accident investigation provides an interactive opportunity to learn more to prevent re-occurrence while engaging staff.
Thirdly, the executive does not have to be the chair but the mere presence provides support, structure and guidance that is often needed to have an effective accident review board. Accident boards should be conducted effectively time wise and efficiently to obtain pertinent information while maintaining a cordial tone. Ineffective boards can be a painful process for both the subject employee and the board. In the situation described in the introductory paragraph, the supervisor acting as the chairperson needed support and guidance that was lacking, not to sway but to have constructive feedback.
Hence, mangers need to attend accident review boards so that they have provide a meaningful concern for employee safety, that they not only want to know what contributed obviously to the event but find out circumstances and procedures that may have contributed to the occurrence, and finally, to assist in the efficiency and effectiveness of the accident review board but not to control it. An accident review board without senior leadership sends a negative message to employees and the board, and creates an ineffective process to eliminate reoccurrences.
*The views and opinions expressed in the Public Risk Management Association (PRIMA) blogs are those of each respective author. The views and opinions do not necessarily reflect the official policy or position of PRIMA.*

By: Dan Hurley, CSP, ARM-P, MS, MPA
Risk Manager, City of Chesapeake, VA (Ret.)
Dan has experience as a risk manager for both a school district and municipalities including a 2 year stint as a practice leader for an excess workers' compensation carrier. Dan is a past PRIMA president and past president of the VA PRIMA chapter. Dan has an ARM-P, is a certified safety professional and has both an MPA and MS from Old Dominion University with a BA from Virginia Tech. Although recently retired after 44 years, starting as a social worker, Dan continues to be involved with VA PRIMA as a board member and with casual part time work.
As a public sector risk manager, I always pay attention to product recalls. These bulletins or headlines usually involve various vehicles (their brakes or exhaust most often) or food products (usually it seems to be lettuce that is the guilty party). I could not think of a recent recall that had involved playground equipment. Since I work as a Certified Playground Safety Inspector (CPSI), I was especially interested in the news of this recent playground recall and decided to do some further research.
The recall that I am addressing is the BCI Burke Merge Playground Climber which had a recall issued by Burke on Dec.19, 2019.
Additional information and a photo of the product is available here:
The three purposes of my blog post are as follows:
- Please check to ensure your playgrounds do not contain a BCI Burke Merge Playground Climber but if so, please take immediate corrective action
“Consumers should immediately stop using the Merge Climbers and block them off from children’s use.”
- To help explain the dangers involved with playground entrapment hazards
The recall of Burke’s Merge Playground Climber is due to entrapment hazard, and I wanted to educate readers that an entrapment hazard may result in a serious injury or fatality to playground users.
More information on playground hazards, including entrapment, is explained (page 15) in the Public Playground Safety Handbook. This document can be found at the U.S. Consumer Product Safety Commission (CPSC Document #325) website at:
https://www.cpsc.gov/s3fs-public/325.pdf
This handbook provides a valuable resource to safety professionals and those who manage or work with playgrounds. Consider bookmarking this website or printing out the document to keep at your fingertips for future reference. If you have playgrounds at various locations you can print copies of the document to distribute. Public entities can order multiple copies for free.
Per CPSC, playground entrapment is defined as:
“Any condition that impedes withdrawal of a body or body part that has penetrated an opening.”
And the following additional information is found on page 15:
“Head entrapment is a serious concern on playgrounds, since it could lead to strangulation and death. A child’s head may become entrapped if the child enters an opening either feet first or head first.”
To say this simply, a serious danger exists because children can be hung up by their heads and/or necks and be unable to free themselves.
- To remind us how to research recalled products
One can research recalls on https://www.cpsc.gov/Recalls
A quick search indicated that there were few recalls related to playgrounds. This is fortunate news for us in the field of public sector safety. Other recalls related to recreation, such as games, swimming pools or hot tubs, can also be found here.
Overall, the website provided a centralized resource for recalls. The site was extremely user friendly, containing many helpful details and simplified the process of sharing the information with your followers on social media.
*The views and opinions expressed in the Public Risk Management Association (PRIMA) blogs are those of each respective author. The views and opinions do not necessarily reflect the official policy or position of PRIMA.*

By: Joann Robertson, CSP, CPSI, CPCU, ARM
Playground Safety Expert, Playground Medic (Hawthorne, NY)
Joann is a certified playground safety inspector who has worked in the field of public sector risk management for over 30 years. Her current responsibilities are safety inspections and networking. Joann's current job is organizing playground inspections and repairs. She is a member of Long Island ASSP and has her BS in environmental science and outdoor recreation.
The shoulder joint is a complex area that can be prone to injuries, particularly for employees working in the healthcare, construction and manufacturing industries.
There is no bone connection between the shoulder blade and the humerus, just cartilage, ligaments, and tendons. The area is fragile and susceptible to injury due to repetitive or monotonous work that constantly utilizes the same arm movement, trauma and disease. Other factors that can increase the risk of a shoulder injury include heavy lifting, stress and depression. Because of these variables, it is crucial that treating physicians use evidence-based medicine to make proper care determinations.
With any shoulder pain, the initial diagnosis is most important. Best practice guidelines for occupational-based medical and disability care, like those established by the Official Disabilities Guidelines (ODG) and the American College of Occupational and Environmental Medicine (ACOEM), provide a good starting point.
For someone presenting with a shoulder injury, the physician should return to basics and spend time inspecting, palpating, and comparing both shoulders to understand the bone structure and any types of degenerative changes that may exist, rule out other diagnoses and address fractures and dislocations.
When treating shoulder injuries, keep the P.R.I.C.E. principle in mind. First, Protect the area and use Relative Rest to minimize utilization of the joint for the first 24 to 48 hours. Apply Ice to active injuries to help with swelling. After 48 hours, alternate use of ice and heat. Compression, using supportive wrapping, should be applied to the shoulder area to help with instability. Finally, use Elevation to decrease inflammation. These guidelines are all evidence-based from ODG and ACOEM.
Approximately 90% of shoulder injuries will require mild to moderate treatment. The first physician visit immediately following the injury may involve changing activity a little and using acetaminophen or an anti-inflammatory. During the second visit, typically a week or two later, the physician may recommend physical or occupational therapy, or a combination, at two to three visits a week for two weeks.
On the third visit, about three weeks to a month later, if things have not improved, the physician may recommend some form of an injection to provide limited improvement to the pain and inflammation and continued therapy and home exercises.
At the fourth visit at around six weeks, in 30% of cases, the physician will do some form of imaging to diagnose tendonitis, bursitis or other soft tissue problems. Finally, after three months, if conservative treatment is not proving effective, the physician may recommend a more aggressive treatment such as surgery or arthrograms.
Applying general guidelines rooted in evidence-based medicine can be an effective way to help reduce the risk of having poor outcomes in terms of the diagnosis and treatment of issues involving the shoulder.
*The views and opinions expressed in the Public Risk Management Association (PRIMA) blogs are those of each respective author. The views and opinions do not necessarily reflect the official policy or position of PRIMA.*

By:
Fernando Branco, MD, FAAPM&R
AVP of Claims and Chief Medical Officer, Midwest Employers Casualty
Fernando is chief medical officer at Midwest Employers Casualty (MEC), a Berkley Company. He has over 30 years of experience in clinical practice and is board certified in physical medicine and rehabilitation, pain, and addiction medicine. He is the former medical director of a multi-disciplinary rehabilitation pain center for the treatment of chronic pain cases – a center of excellence recognized by the American Pain Society. In his current role at MEC, Dr. Branco leads a team of medical management consultants handling complex workers’ compensation claims to help employers and injured workers achieve better outcomes.
In the ever-growing list of issues a police officer must be prepared for, responding to structure fires may fall way down the list, but maybe it shouldn’t. The risks and exposures from fires are growing every day, and police officers are often the first emergency personnel to arrive.
Police officers receive a few hours of training in firefighting during their academy days, and that is often the last time the concerns are raised until an officer gets hurt. Only then do police departments begin to look at the hazards to their officers. Firefighters across the United States are recognizing the change in fire dynamics due to light-weight construction and the prevalence of plastics and urethane elements of building furnishings. These changes are making the decisions to enter a burning building much more difficult than in the past.
Hazardous exposures to toxic smoke are having an increasingly rapid impact on , and the chemical makeup of the smoke and combustion by products are leading to more respiratory respondersissues and long-term damage than ever before. While these issues are in the forefront of safety discussions in the fire service, they often are lost in the shuffle when law enforcement discusses their primary safety concerns.
Police departments should educate their officers about the changing dynamics of fire today to ensure that officers have made a thorough and correct assessment of conditions before deciding to enter a building. Several cases have been documented where officers entered to search for or rescue occupants, only to find the police officers in need of rescue themselves. These officers have experienced career-ending, if not life-ending, injuries from the well-meaning efforts to enter a burning structure. Successful rescues also lead to the misguided belief that the officers will have time to affect a rescue, when the time from fire inception to building collapse has never been shorter in residential buildings.
Police departments should be reviewing and updating their policies for fire responses to ensure that officers know their role once on scene and understand the ramifications of making the wrong decision regarding entering a burning building, even when there are people known to be trapped within the structure. The policies should provide guidance on issues that will help with the suppression and investigation of a fire. Patrol cars should be parked so as not to hinder the fire department’s access to the building, including bringing water from a nearby fire hydrant. Vehicles should be parked with their dashcam (if equipped) focused in the direction of the fire to memorialize fire growth and movement, something that will be very valuable to the origin and investigation of the cause.
Police officers should be taught how to “size up” the fire and the structure to communicate critical information to the fire department. With this “size-up,” a determination can be made whether it is safe to try to enter the structure, or if entering will lead to an immediate danger to the life and health of the police officer. Guidance and education will be the only tools available to the officer when s/he tries to determine her/his best course of action.
These thoughts just scratch the surface on what is needed for police officers to be prepared to safely respond to fire emergencies with methods that not only protect civilians, but also themselves.
*The views and opinions expressed in the Public Risk Management Association (PRIMA) blogs are those of each respective author. The views and opinions do not necessarily reflect the official policy or position of PRIMA.*

By: Kenneth Child
Risk Control Supervisor, PMA Companies
Summary of Qualifications
Kenneth is a risk control professional with over 30 years in the industry, the past 18 focused on public entity risk control and reduction. He is also:
Volunteer firefighter. Ex-chief with over 36 years of fire service experience.
Volunteer EMT with over 40 years of experience responding to medical emergencies including treating victims of fires and smoke inhalation
Member of NJ State Firefighter Safety & Health Advisory Council
Responsibilities
Kenneth supervises a team of risk control consultants, providing guidance and training to more than 100 public entities across New Jersey and supporting consultants throughout the US for PMA Management Corp. This team provides consultations regarding all aspects of risk control and safety for their member clients through their relationship with their respective self-insured insurance funds.
Education
BS - Business Management Monmouth College (now University) West Long Branch NJ
Certified Safety Professional - BCSP
Associate Risk Management - Public Entities
Associate Loss Control Management
NJ State Certifications: Firefighter 2/ Fire Officer 1/ Fire Official/ Fire Instructor 1/ Fire Investigator/ EMT-B
Sleep is a biological need for life and health. Like the need for food, too little or too much has significant mental and physical health consequences. Most adults need seven to nine hours of good-quality sleep every 24 hours to perform during well.
When you lose sleep, you build up sleep debt that will seriously impair your performance at work, and the only way to pay off this debt is to get enough sleep.
Management may perceive fatigue as a behavioral problem – an employee’s lack of commitment to the job, a poor attitude, or lack of willpower. Our pervasive cultural mentality embraces the notion that fatigue can be conquered by sheer will or perhaps that it is a badge of honor. This position, of course, ignores the growing body of research demonstrating the safety and productivity consequences of fatigue and sleep deprivation.
Creating a culture in the workplace that recognizes the importance of fatigue management is critical. As we consider the future of work, now is the time for employers to address sleep deprivation and fatigue to support their employees’ well-being – and ultimately their organizations’ success.
It has been estimated that 13% of all workplace injuries are related to sleep deprivation and fatigue.[1] And, according to the National Safety Council, highly fatigued workers are 70% more likely to be involved in incidents that result in injury, and workers who report disturbed sleep are nearly twice as likely to die in a work-related incident. This is because mental fatigue leads to distortions that influence decision-making. For example, making decisions automatically, without conscious thought. Our brains are very selective on what to focus on and this is more limited with fatigue. We think we see everything in view, but we don’t.
Also, when we’re cognitively fatigued, we are more likely to find easier paths. We believe we can multitask, but when we try, we make more errors.
There are many causes of fatigue that result from workplace factors and those related to personal lives. Categorically, causes of fatigue include physical, mental and environmental loads. Forceful exertion, repetitive motion and awkward postures are examples of physical loads that can result in fatigue, while stressful coworker relationships, lack of decision autonomy, shift work and irregular work hours can drive mental fatigue. Temperature extremes, noise and low lighting are examples of environmental loads.
Shift work is another area of focus. Employers should be aware that the beginning and ending of shifts are the most dangerous. Occupations that involve non-traditional work hours comprise about 15% of US workforce, so careful assessment of the timing of shifts and rotations is essential. Allowing time for use of caffeine has been shown to be effective – especially when combined with 10 to 15 minutes of napping. Use of caffeine just before a short nap can allow sleep before the caffeine begins to have affect. Other steps can include providing adequate lighting and temperature control when possible.
Supervisors will likely need to rely on observation and experience to identify when workers are experiencing fatigue and possible presenteeism. Signs of fatigue include acute or chronic sleepiness, yawning, irritability, reduced memory or concentration, low motivation, mistakes and lapses in communication and judgment. Supervisors should be trained on how to spot these signs and intervene.
Supervisors should also clearly reinforce with employees that it is their responsibility to arrive at work rested and ready to provide full effort. Employees need to evaluate their sleep and seek help for sleep disorders. If they are having problems obtaining adequate amounts and/or quality of sleep, they should follow up with a healthcare provider to seek assistance. Sleep hygiene techniques include maintaining a regular sleep schedule, avoiding stimulants and other substances that impact sleep before bedtime and getting adequate exercise.
Workers who are fatigued or sleep deprived simply will not be as safe or productive as workers who are not. Employers can play a critical role in keeping their employees safe by fostering a company culture that supports employee well-being – including sleep.
[1] Uehli K, Mehta AJ, Miedinger D, Hug K, Schindler C, Holsboer-Trachsler E, Leuppi JD, Künzli N Sleep Med Rev. 2014 Feb; 18(1):61-73.
*The views and opinions expressed in the Public Risk Management Association (PRIMA) blogs are those of each respective author. The views and opinions do not necessarily reflect the official policy or position of PRIMA.*

Mark S. Williams, DC, MBA, DACBOH
Medical Director, Claims, The Hartford
Responsibilities
Mark explores innovations in processes and products that are supported by scientific evidence in order to serve The Hartford employees and external customers. He provides consultative insight and leadership on health care matters across all products at The Hartford. This includes claims with complex medical issues, as well as thought leadership and education with clinical and claim staff.
Mark also provides guidance to impact health and wellness and empower The Hartford's customers to prevail both in and out of the workplace. He partners with business units to provide the best and in-depth answers to customers' most pressing questions.
Business Experience
Mark has been involved in healthcare, as well as disability and workers' compensation insurance industries for over 30 years.
Professional Affiliations
- American Chiropractic Association
- American Chiropractic Board of Occupational Health
- American Chiropractic Association Opioid Task Force (Chair)
- IAIABC Medical Issues Committee
- IAIABC Work Disability Prevention and Return-to-Work Committee
Education
Mark has a Doctor of Chiropractic degree as well as an MBA. He is board certified in occupational health and ergonomics, and has a bachelor degree in human biology.
There have been many claims filed that do not, at first glance, appear to have a large exposure. In the public sector, sometimes the insured’s reputation has been magnified by the media after a detrimental has taken place. When a case is reported that does not appear to have a large exposure, the plaintiff attorney can do research on a town, a school district or a college to see if there is any negative reputation that can be used. Today, deep research is conducted for any related claims, especially in police related prior claims. It is always important to have a good defense attorney, but there have been a few times that the defense attorney and the claim adjusters do not think a claim is going to become a larger exposure, since some prior events or some other small aspects do not appear to raise the value of the case. If the plaintiff attorney is not willing to discuss a case settlement and has a bigger desire to take the case to court, there are several reasons he or she may want a jury to listen to the case.
A court jurisdiction is another thing to study. Sometimes an attorney will want to file a suit in the federal court for several reasons. After a case is finished in federal court, the plaintiff attorney can file a demand for a large amount of his fees. Even if the final judgement is not real high, they can ask for as much as a million dollars of fees. On the other hand, the plaintiff attorney may prefer to file in the area’s county court. Some county jurisdictions around the country have been known to provide a very large verdict amount, the people selected to be on the jury can be known to have been in juries that have always provided a larger amount demanded by the plaintiff attorney. There are other local jurisdictions that have been more willing to respond better to the defense case. This jurisdiction may find the insured guilty, but they may not always vote for as large as the demand the plaintiff attorney seeks. This is one of the aspects that need to be thought about as the case begins to move forward. If the plaintiff attorney is not willing to consider discussing a settlement amount, just be aware you may be going to court for these reasons.
We are now moving to a list of some more things that need to be considered before making your strongest decision regarding the exposure you may be facing. Some of this list may not appear to be important, at first, but they can possibly have a strong impact.
Newspapers and Internet Comments
After an incident occurs, it is always wise to search social media and read your on-line local newspapers that allow readers to add commentary at the end of the article. Those comments can help you understand what your community thinks about the incident.
The majority of highly publicized incidents these days normally involve police departments, but it is not only police related events that need to be carefully reviewed. Allegations of sexual abuse, improper employment management issues, insufficient property maintenance and many other areas can generate a large claim. If you have several annual events that can generate crowds, make sure events are properly planned and set up securely. The file handlers need to gather as many strong facts as they can and must be ready to respond to the media when media seeks more information from the public entity and schools. If the investigation is not commenced fast enough, the media will post a negative response if an entity is not ready to respond to their questions.
Your Reputation
Public entities and school districts can generate a lower reputation if a number of incidents have occurred that have generated negative publicity from the media. A negative reputation can make the value of your case increase higher than expected because a jury might award a higher verdict in an attempt to punish an entity or school district because of their reputation. A negative reputation can have an impact, even if the reputation was not built on a similar incident, you are currently dealing with.
Plaintiff Attorney’s Reputation
Plaintiff attorneys’ positive reputations can grow higher based on the publicity generated regarding any earlier cases regarding a large settlement or verdict amount. In addition, many firms are now often seen on TV commercials expressing how important it is for an injured party to hire them. They also often make it sound like a carrier is against taking care of an injured person.
*The views and opinions expressed in the Public Risk Management Association (PRIMA) blogs are those of each respective author. The views and opinions do not necessarily reflect the official policy or position of PRIMA.*

By: Richard Spiers, CPCU, ARM, ARe, AIC
Consultant, Spiers Consulting, LLC
Richard has been in the insurance industry since 1980 and was a claim executive in the reinsurance and excess marketplace since 1985. He was with Genesis Management and Insurance Services for over 20 twenty years. He is currently doing claim consulting work. Richard has extensive experience handling the wide array of claims faced by public entities, K-12 school districts and the higher education sector. Based in Chicago, he has also worked for Transamerica Insurance Group, Northbrook Excess and Surplus Insurance, CNA and Allstate Reinsurance. He is a graduate of Northern Illinois University, a member of the Society of CPCU, and holds associate designations in risk management, claims, and reinsurance. Richard has been developing and presenting insurance industry-related training sessions to a variety of client and industry groups for over 25 years.
A Florida town pays $600,000 to hackers who seized control of the city’s computer systems, a breach that began in the police department.
Computer screens at a dispatch center go dark, jail cell doors can’t be opened remotely and sheriff’s deputies can’t look up license plates as a cyberattack hits Jackson County, Ga.
An airport in Albany County, NY, pays a “less than six-figure” ransom to restore data that was encrypted by a virus spread on the airport authority’s servers and backup servers.
These are just a few examples of the fast-growing threat of ransomware attacks on local governments and public safety agencies. The U.S. Conference of Mayors cites at least 22 major ransomware attacks against local governments in 2019, causing service disruptions and costing millions of dollars in ransoms and repairs. Experts say the actual number of attacks is probably much higher than reported, because many agencies that have paid ransoms do not want their names released for fear of becoming a repeat target.
While ransomware is a key concern for any business, such attacks on local government and public safety agencies threaten lives, not just the bottom line. Why are public safety agencies a target for ransomware attacks, and why are these attacks growing? Perhaps most important, how can local governments protect themselves?
Why Ransomware Targets Public Safety
Cyber criminals have forced U.S. hospitals, schools and cities to pay hundreds of millions in ransom to regain access to critical files. In the most widely reported case, two individuals from Iran were indicted after allegedly collecting over $6 million in ransom payments from municipalities and other victims. The ransomware they developed was known as “SamSam” and the attackers specifically targeted public entities, hospitals and municipalities.
But why? In the SamSam case, then-Deputy Attorney General Rod Rosenstein stated, “They knew that shutting down those computer systems could cause significant harm to innocent victims.”
So the first thing to consider is that public safety agencies and local governments make good targets for ransomware because hurting them has a multiplier effect, with potentially life-threatening consequences.
Media accounts of how ransomware has hurt public safety agencies can also lead to an increase in attacks. In many communities, negative publicity surrounding law enforcement has generated anger, which can in turn make agencies more vulnerable to ransomware attacks. Local governments are also an easy target because they often rely on aging computer systems that are easier to access and damage.
When ransomware attacks first started hitting public safety agencies, it was not common to pay ransoms. After all, law enforcement agencies aren’t typically inclined to allow criminals to dictate the terms of engagement. But when those payments were refused, files were never seen again. Now, the increasing number of attacks are, more often, forcing agencies to pay.
Anatomy of an Attack
Much of the ransomware affecting the United States originates in Russia and other parts of Eastern Europe. The FBI is investigating actively, but it has been difficult to find details on the members of the “ransom gangs.” Because all that’s needed is some computer equipment, technological expertise and access, hackers can live almost anywhere, connecting virtually across the world and evading detection for years.
A typical ransomware attack goes like this: An email is received with what appears to be an important link to click on or an attachment to open. When the recipient dutifully clicks or opens, their files become encrypted. This encryption can spread through the agency’s or municipality’s networks until everything gets locked.
The user will usually see a message indicating their files are being held hostage; they may see a clock ticking with a countdown to the deadline for paying the ransom. The ransom is normally demanded to be paid via Bitcoin, an untraceable digital currency. The message will also often provide instructions on how to access Bitcoin. When the ransom is paid, the agency will get an emailed “decryption key” that unlocks the system. If the agency won’t pay, the hackers threaten to delete the files.
It can be tempting to quickly pay a ransom when the amount is just a few hundred dollars, but the examples cited at the beginning of this article show that is not normally the case. Hackers know who they’re targeting; they understand municipalities have access to funds an individual might not. Another factor to consider when deciding whether to pay a ransom is that some experts believe ransomware often funds terrorism and organized crime—clearly contradictory to the missions of public safety agencies.
Finally, consider the message you’re sending to the hackers when you pay a ransom. The FBI acknowledges most victims who pay ransom do get their files back. But they note every time a payout is made, it encourages hackers to attempt more attacks.
*The views and opinions expressed in the Public Risk Management Association (PRIMA) blogs are those of each respective author. The views and opinions do not necessarily reflect the official policy or position of PRIMA.*

By: Richard Spiers, CPCU, ARM, ARe, AIC
Consultant, Spiers Consulting, LLC
Richard has been in the insurance industry since 1980 and was a claim executive in the reinsurance and excess marketplace since 1985. He was with Genesis Management and Insurance Services for over 20 twenty years. He is currently doing claim consulting work. Richard has extensive experience handling the wide array of claims faced by public entities, K-12 school districts and the higher education sector. Based in Chicago, he has also worked for Transamerica Insurance Group, Northbrook Excess and Surplus Insurance, CNA and Allstate Reinsurance. He is a graduate of Northern Illinois University, a member of the Society of CPCU, and holds associate designations in risk management, claims, and reinsurance. Richard has been developing and presenting insurance industry-related training sessions to a variety of client and industry groups for over 25 years.
The field of Enterprise Risk Management (ERM) has long used heat maps as a means to organize, define and rank risks that impact, or could potentially impact, an organization. They are presented to an organization’s leadership to assist in visualizing an organization’s risk exposure, provide a big-picture perspective on risk, and guide prioritization of risks.
While heat maps can depict the volume of risks and provide slight context about an organization’s general exposure to risk, heat maps do not provide meaningful data or detail to inform decision-making. When presenting risks in the form of a heat map based on an assessment of a risk’s likelihood and consequence, it is not easy to infer which risks truly require prioritization; multiple risks often fall into the same cell of the map, and typically within the same range of risk exposure.
Sample Risk Heat Map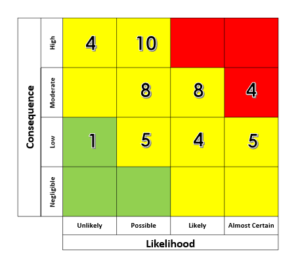
In reviewing a heat map, one is left wondering: how do we distinguish among multiple risks in the same cell? In the same quadrant? Within the same color/level? Which should be prioritized? In short, a heat map generates more questions than it answers.
To generate meaningful data from the risk assessment process and effectively enable ranking of risks, organizations should consider incorporating an additional risk factor into their assessment process that can account for the risk appetite and strategic priorities of an organization’s leadership. This risk factor should be assigned by the organization’s leadership team, with full visibility to the consequence and likelihood values assigned to the risk. This additional risk factor, which we’ve entitled “urgency”, asks the question, how soon does our organization need to prioritize this risk?
The criteria for the risk factor can be adapted for your organization and should be designed to ensure your organization’s leadership takes into account their strategic priorities and risk appetite. Similar to the valuation provided to consequence and likelihood categories of rating risks, the responses to the question are aligned with a numerical value, with the soonest timeframe aligned with the highest numerical value, and the longest timeframe being aligned with the lowest numerical value.
With the three risk factors evaluated, the organization can then generate an overall score for the risk by multiplying as follows:
Likelihood X Consequence X Urgency
Risks can then be ranked and sorted by the overall risk score, clearing defining which risks require prioritization. The resulting prioritized risks have then been evaluated based on the impact to the organization as well as the risk appetite of the organization.
*The views and opinions expressed in the Public Risk Management Association (PRIMA) blogs are those of each respective author. The views and opinions do not necessarily reflect the official policy or position of PRIMA.*

By: Christine Packard
Director, Enterprise Risk Management, University of Massachusetts - President's Office
Having spent more than 15 years in the field of emergency management, including seven as the deputy director of the Massachusetts Emergency Management Agency, Christine joined the University of Massachusetts in August 2019 as its first dedicated director of enterprise risk management. In her role as ERM director, Christine is responsible for the system-wide enterprise risk management program, working with the five UMass campuses and the system office to identify and assess risk impacting the UMass system, and ensuring implementation of mitigation strategies.

By: Olivia Watson
Analyst Enterprise Risk Management, University of Massachusetts - President's Office
A graduate of the University of Massachusetts - Amherst, Olivia joined the University of Massachusetts in October 2021 having spent two years in the fields of public health emergency preparedness and emergency management.
Almost every week, media outlets report a new case of child sexual abuse taking place in a youth-serving organization setting. To better prepare your organization to prevent child sexual abuse, here are five things educational leaders should consider:
- There is no profile for a child sexual abuser. You cannot classify child sexual abusers by age, economic status, ethnicity/race, gender, marital status or sexual orientation, according to Child Sex Offenders Typologies (Simons, 2015). Therefore, anyone could be a child sexual abuser. By being aware that anyone could inflict harm upon minors while they are in the care, custody and control of a youth-serving organization, educational leaders can plan strategically to prevent incidences of abuse from occurring.
- Child sexual abusers work methodologically to gain access to or be near their preference without raising suspicion. Child sexual abusers may choose to work as custodians, IT professionals, photographers or security officers. Because there is no way to identify a child sexual abuser by appearance or any other variable outside of a criminal background check, child sexual abusers, who do not have a record of arrest or a conviction that would disqualify them from being hired, may already work at your organization.
- Child sexual abusers groom their preference to gain their trust to view their relationship as permissible and reciprocated (Groth,1983). It would behoove educational leaders to respond with caution when individuals responsible for working with minors begin to "blur the lines" between professional conduct and inappropriate behavior. Inappropriate behavior would include insisting youth address a caregiver as "grandma" or "uncle." This persistence to be addressed by a familial term rather than their name may cause minors to think the relationship with their caregiver is a personal relationship rather than one that should be professional.
- Child sexual abusers maintain very private personal lives. Most abusers experienced some form of abuse or neglect (emotional, physical, sexual) during their childhood and may have engaged in sexual activity with themselves, others or even animals at a young age (Simons et al., 2005). Because of their need to maintain their privacy, "child sexual abusers assault to alleviate anxiety, loneliness and depression" (Simons, 2015). Although a child sexual abuser may seem congenial and may even be considered a "team player," their coworkers and colleagues may not know much about them outside of the work setting.
- Child sexual abuse data and reporting often appear inconsistent. The reason for this disparity is that the National Child Abuse and Neglect Data System (NCANDS) only tracks child abuse and neglect inflicted by caregivers in the home (parents, household members), while incidences of child maltreatment by out-of-home caregivers fall under state and local law enforcement. Those data systems are handled and monitored by separate entities and do not necessarily provide a complete perspective of child abuse and neglect.
Effective youth protection systems help educational leaders increase awareness of child abuse and neglect within youth-serving organizations. In addition, effective youth protection systems enhance reporting procedures, which is key to preventing child sexual abuse.
*The views and opinions expressed in the Public Risk Management Association (PRIMA) blogs are those of each respective author. The views and opinions do not necessarily reflect the official policy or position of PRIMA.*

By: Joaquina Scott Kankam, Ph.D.
Director and Senior Consultant, School of Solutions
Summary of Qualifications
Joaquina Scott Kankam, Ph.D., is the director of School of Solutions, a consultancy specializing in youth protection. Not only is Joaquina an expert in youth protection compliance and risk management, but her practical experience has made her a leader in understanding the needs of youth-serving organizations.
Joaquina has worked in education for almost twenty years to improve the lives of others. In addition to being an educator (K-12 & Higher Education), Joaquina has presented at several national association conferences and participated as a panelist in several discussions regarding youth.
Responsibilities
Dr. Scott Kankam works nationally to assist youth-serving organizations with protecting minors from abuse and neglect. She helps to create a better tomorrow by auditing and enhancing youth protection policies and policies.
Business Experience
Dr. Scott Kankam's experience includes enhancing and creating an awareness of the Six Effective Practices of the Youth Protection Enterprise Risk Management System®. The Youth Protection ERM System® identifies unknown and uncontrolled risks associated with hosting, operating or sponsoring programs for minors.